PhishDefense
Phishing Training


Phishing attacks are one of the most common and dangerous cyber threats facing organizations. Three billion spoofed emails are sent every day, and phishing is involved in 36% of breaches (see Security Awareness Training Statistics & Trends.) During the COVID-19 pandemic, phishing has reached stratospheric levels, increasing over 600 percent.
With the ever-increasing frequency and sophistication of cyber attacks and phishing scams, the cyber risk is constantly growing. Even the most sophisticated security software and hardware isn’t able to identify and block all phishing attacks, and prevent them from reaching your employees. Phishing training is your best phishing protection, providing the knowledge and cyber skills employees need to protect themselves and your organization against phishing attacks.
PhishDefense Phishing Training from Security Mentor provides the tools you need to combat phishing.
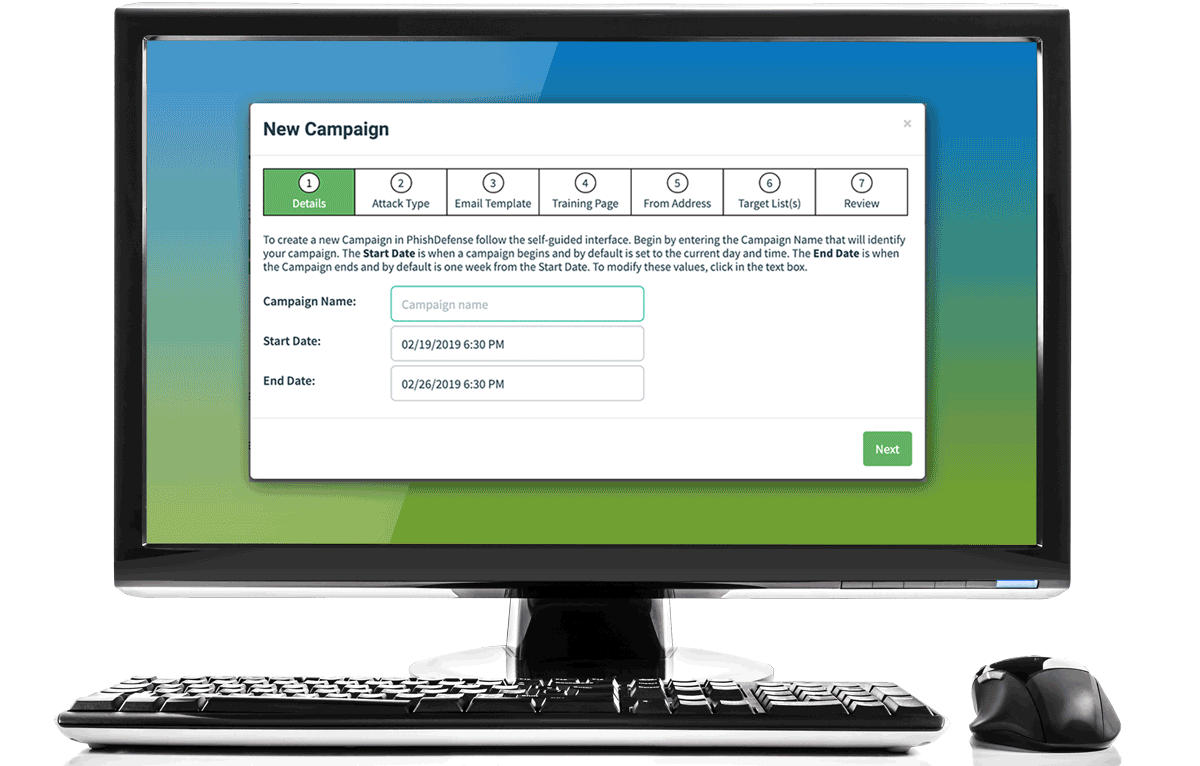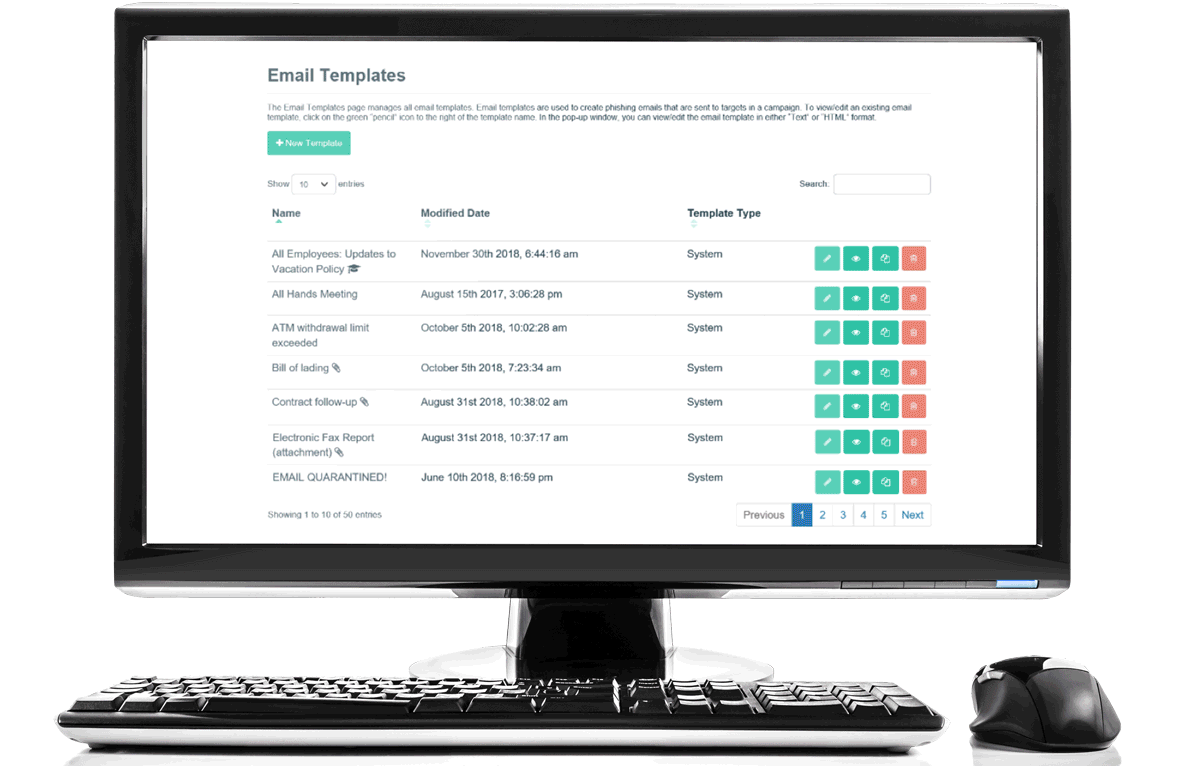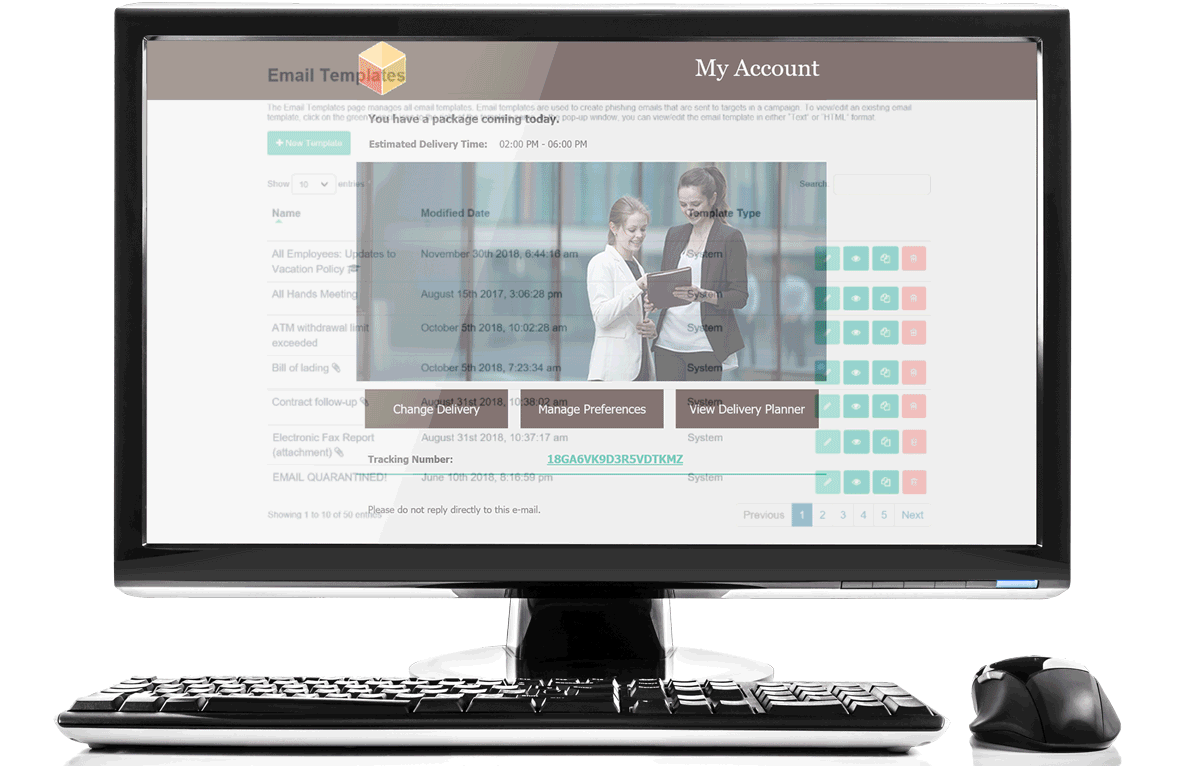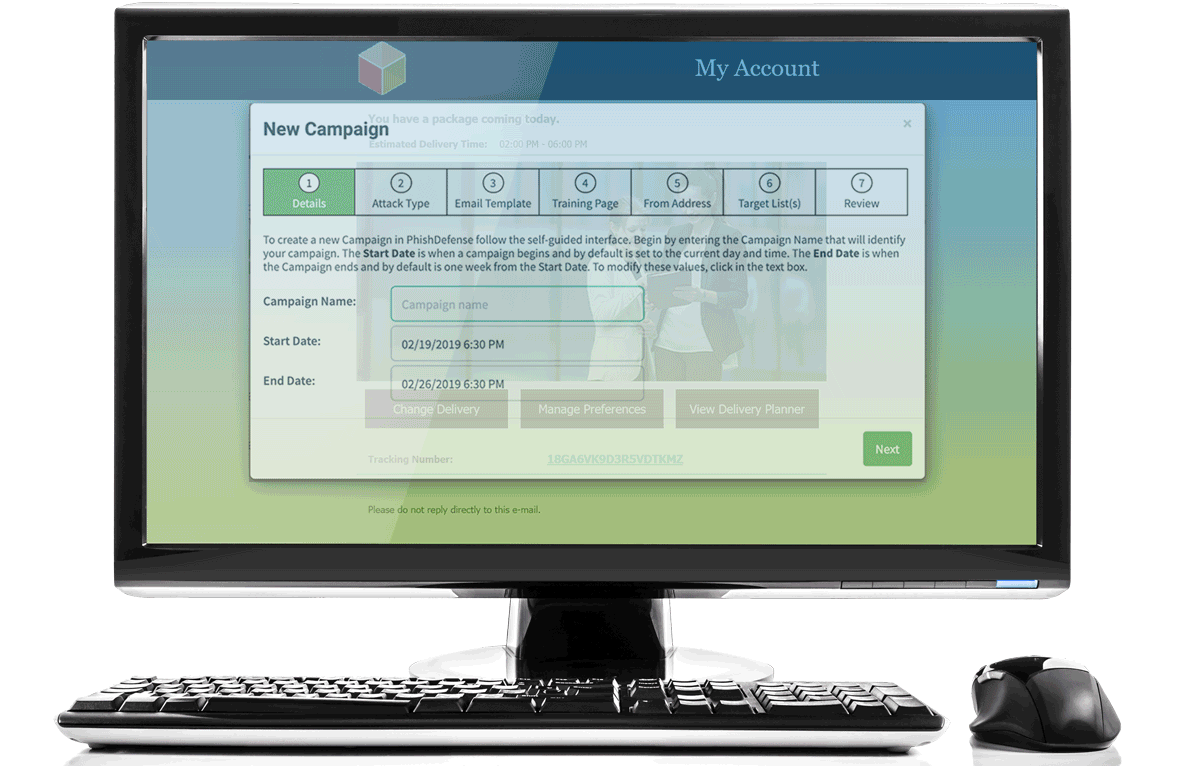
Run Phishing Tests with Our Phishing Simulator
The cloud-based PhishDefense Phishing Simulator enables you to train your employees to spot phishing scams and become resistant to phishing by simulating real phishing attacks.
Each phishing simulation starts with setting up a phishing campaign, including selecting the following: group of employees to be targeted, phishing template, sending domain, and training page. You can choose a phishing template from our catalog of phishing templates that simulate real-world cyber attacks (e.g., phishing, spear phishing, ransomware, BEC), or create your own custom phishing templates. On the date specified, the phishing campaign is automatically launched.
Assess Employee Phishing Vulnerability & Train
While your phishing campaign runs, PhishDefense tracks each phishing email and how your employees interact with it. Our system quickly identifies vulnerable employees, those that are phished, and provides real-time training alerting the employee to their mistake, and creating a learning moment from a potential cyber security incident.
PhishDefense:
- Tracks employee interactions with phishing emails including reading a phishing message, clicking on a phishing link, opening a malicious attachment, or filling in a web form
- Redirecting at-risk users to targeted phishing awareness training
- Helps employees become phish aware by showing how they could have identified the phishing attack
For those organizations that prefer not to let employees know they were phished so they can provide individual training later, we have a stealth mode too.
Integrated with PhishDefense Phishing Training, the Security Mentor Security Awareness Training program includes an outstanding phishing training course that teaches employees what phishing is, how phishers use social engineering techniques to manipulate them, how to spot a phishing email, and what to do if you think you were phished.

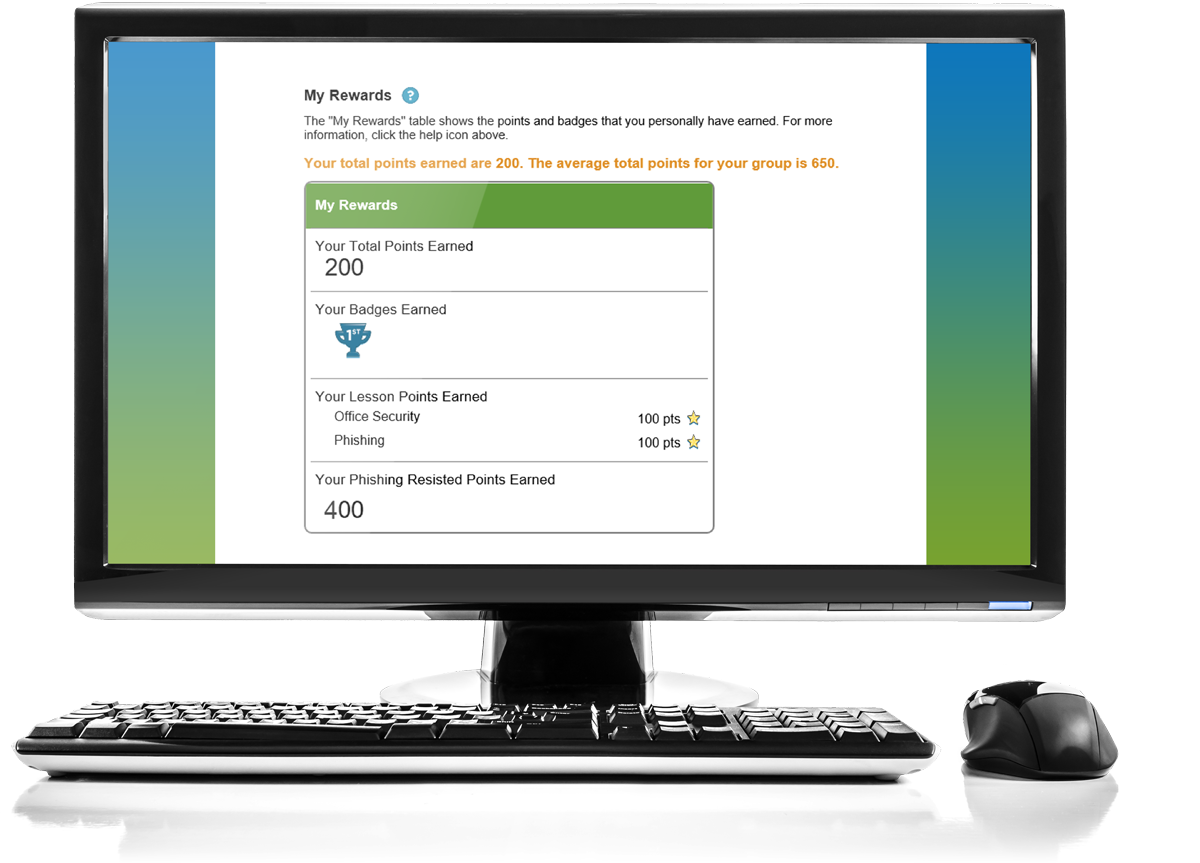
Incent Positive Employee Behavior
Too often phishing training becomes a tool to punish employees who fall victim to phishing scams.
Security Mentor believes that phishing awareness training, like security awareness training, should be about positive reinforcement. PhishDefense rewards positive behavior using gamification.
- When employees identify a phishing email and don't fall for a phishing test, they earn points for their phish resistance, providing an incentive for the desired behavior.
- Group competition enables departments, divisions, or targeted groups to engage in friendly competition to see which group is the most phish resistant and cyber aware.
Develop Organizational Phishing Awareness
Phishing campaigns should be run regularly and often.
PhishDefense enables you to develop targeted phishing campaigns, and schedule and conduct phishing tests over time. Its powerful dashboard tracks how your phishing campaigns are doing and assesses whether you are lowering your organizational cyber risk.
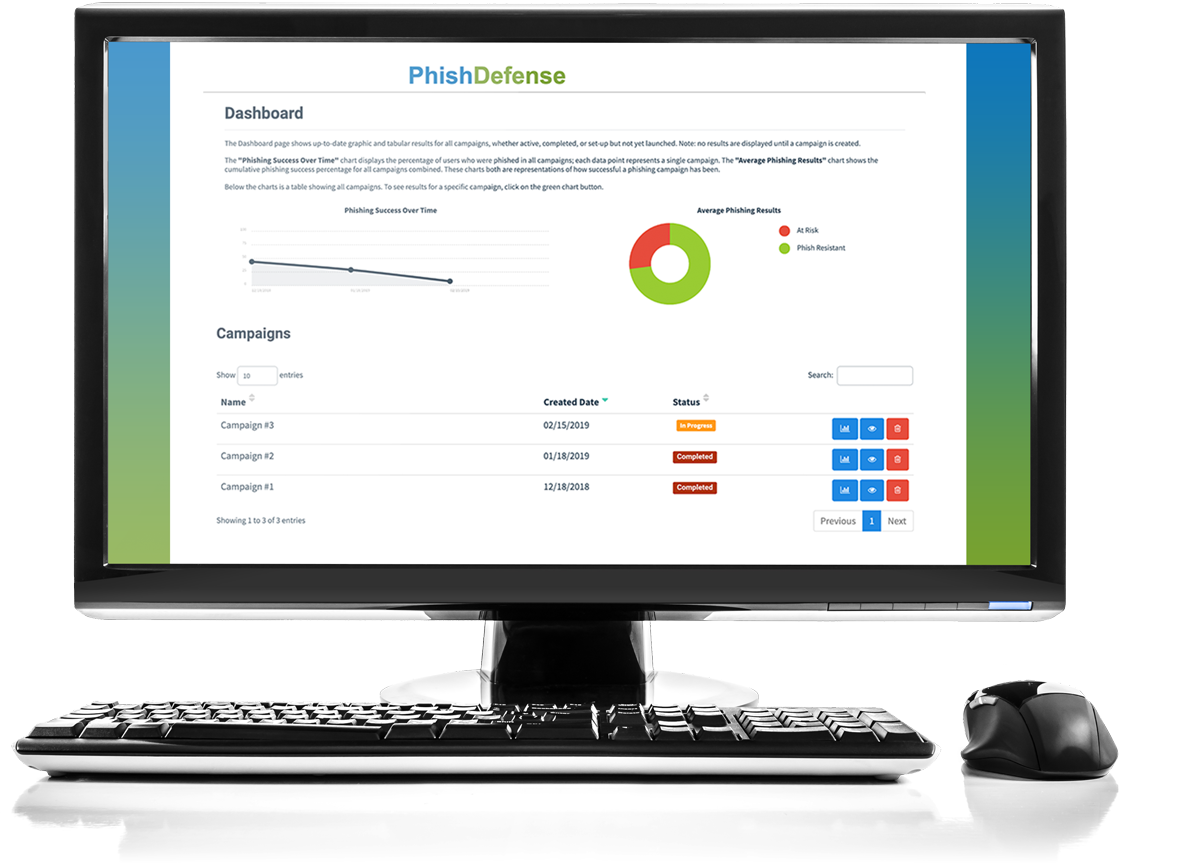
Phishing is a type of cyber attack in which social engineering messages are sent by email, text message, voice, or posted as content on social media sites, with the intent of tricking victims into clicking on a phishing link, opening a malicious attachment, or taking other actions that are against their best interests. The cyber criminal's goal in a phishing attack is to steal valuable information such as identity credentials or financial information, or to install malware, like ransomware, on the victim's computing device.
Smishing, or SMS phishing, is a type of phishing attack in which a social engineering message is sent via a phone text with the goal of tricking the victim into revealing sensitive personal or financial information, or installing malware. Smishing messages often contain phishing links or phone numbers to call, but can also be a Business Email Compromise (BEC) attack. Smishing is a particularly successful form of phishing attack because it plays on the user's trust of their mobile device and phone number. Smishing has accelerated greatly in recent years, and shows no sign of abating.
Vishing, or voice phishing, is a type of phishing attack in which the phisher, pretending to be a trusted organization, calls a target and attempts to get them to disclose sensitive personal or financial information over the phone. Vishing attacks often utilize Caller ID Spoofing to hide their real name and phone number.
Look for these phishing clues in the message:
- The sender (From address) is unknown, or the message is unexpected
- The sender appears to be someone you trust, but the domain is not legitimate
- The greeting and/or the content are generic
- There are grammar or spelling errors in the message
- The actual destination of the URL doesn't go to where it should or is unknown
- The message threatens you, tries to scare you or entices you with free offers
- There is an unexpected or suspicious attachment
- You are requested for private information like credentials or financial account numbers
To protect yourself from phishing attacks, run anti-malware software and keep it updated.
A phishing test is a form of cybersecurity training, where organizations send simulated phishing emails, also known as phishing tests, to their employees. These simulated phishing emails are designed to look like real phishing messages that employees might receive. Through the phishing tests, employees are taught both to recognize a phishing attack, and not to engage in risky behaviors related to unexpected or unsolicited messages (e.g., clicking on links, opening attachments and filling in web forms).
Phishing campaigns should be run frequently enough to test employees' cyber resilience to phishing and to expose them to the new phishing attacks that cyber criminals are constantly introducing. The consensus from security professionals is that a phishing campaign should be run at least monthly, and ideally more frequently.
Phishing training focuses on teaching employees how not to get phished. Phishing is one of the leading causes of cybersecurity incidents, so teaching about phishing is critical. However, phishing is only one of a multitude of cyber threats and cyber risks that employees face every day. Organizations whose only type of cyber security training for employees is phishing simulations leave themselves vulnerable to data breaches and cyber security incidents which could be caused a multitude of other cyber threats including weak, shared, or reused passwords, lost or stolen mobile devices, inappropriate use of cloud accounts, connecting unauthorized devices to the networks, and exposure of sensitive information, just to name a few.
- A lack of stakeholder support or clear goals for the phishing program
- Failing to communicate with employees prior to phishing program launch
- Not establishing an initial baseline for the susceptibility of employee to phishing attacks
- Conducting phishing campaigns too infrequently and without an organized plan
- Embarrassing or punishing employees who were phished, or otherwise making phishing training punitive
- Failing to provide follow-up training when an employee falls for a phishing test
- Not regularly analyzing the results of phishing campaigns or performing deeper analysis on an annual basis
Ransomware is a type of malware (malicious software) that encrypts the files on a computer, but can also encrypt the computing system itself. The cyber criminal then demands that a ransom is paid to get the decryption key. Ransoms are usually required to be paid in a cryptocurrency, like Bitcoin. Another tactic ransomware attackers use is to threaten to sell or publish stolen sensitive data on the Dark Web, if the ransom is not paid. This tactic is used when the data holds intrinsic monetary value or its publishing could be embarrassing to the owner. More recently, ransomware attacks using the combination of these two tactics, called double extortion ransomware, have become more prevalent. In double extortion ransomware, files are exfiltrated before they are encrypted. A ransom is demanded to be paid for the data decryption key and then a second ransom is demanded in order to stop the exposure or selling of the exfiltrated data.
Focus on preventing, and preparing for, ransomware by implementing these cyber security best practices.
- Ransomware usually begins with an employee clicking on a phishing email link or opening a malicious attachment. The best cyber defense is to provide general security awareness training, as well as targeted phishing training, that teaches employees how to avoid phishing scams.
- Keep all end user software updated, including workstation operating systems, applications and browsers. Run anti-malware and other anti-phishing software. For IT infrastructure, keep all server, network and system software updated.
- Carefully configure servers, systems and networks, including changing default passwords, turning off unused services, and closing unneeded ports.
- Make frequent backups that are stored offline or on a separate cloud service. Test backups on a regular schedule to ensure that they can be accessed and recovered.
- Prepare a Cyber Incident Response Plan, including the people, processes, and technology, which will be implemented if a cybersecurity incident occurs. The Stop Ransomware website by the Cybersecurity & Infrastructure Security Agency (CISA) provides useful resources for combating ransomware including a downloadable ransomware prevention guide.
A Business Email Compromise (BEC) attack is a type of phishing attack, where a cyber criminal impersonates a business executive within an organization by sending an email to an employee asking them to take an action that will result in a business compromise. The wire transfer of funds to a malicious account, payment of a fraudulent invoice, or exposure of sensitive information are a few examples of the endgame of BEC attacks.

