Unrivaled Cyber Security Awareness Training for Employees
High quality, interactive, engaging cyber awareness courses combined with easy-to-implement phishing training equips employees with the knowledge and security skills they need to be cyber secure.

Security Awareness Training Platform
Our comprehensive platform provides a full suite of services that ensures the success of your security awareness program.
STEP ONE
Transformative Security Awareness Training
Drive real behavior and culture change using our powerful Brief, Frequent, Focused learning system combined with our compelling, relevant, and impactful security awareness training. Each security awareness training lesson includes serious games and innovative interactions that equip your employees with the knowledge and cyber skills they need to protect themselves and your organization from cyber threats, phishing attacks and ransomware — as well as their own cyber mistakes.
STEP TWO
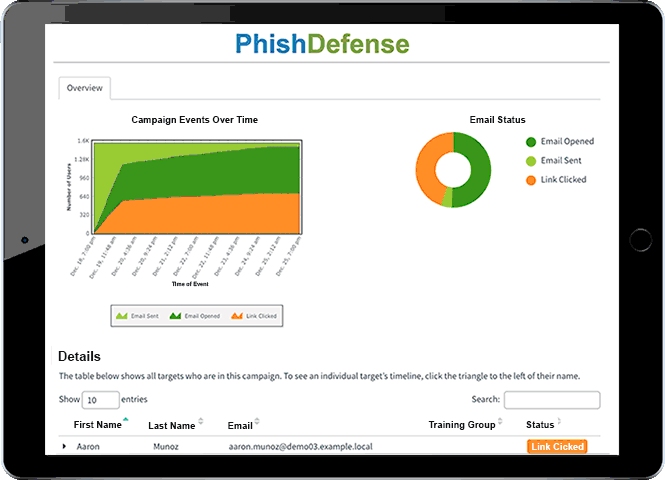
PhishDefense Phishing Training
Send phishing tests and identify vulnerable employees susceptible to phishing attacks using the PhishDefense phishing simulator; then provide real-time phishing training that turns employees' security mistakes into learning experiences. Effortlessly deploy phishing campaigns using our simple, intuitive interface and simulate phishing, spear phishing, ransomware and BEC attacks. Use our pre-built phishing templates, or create your own custom phishing templates. Easily track employee behavior, and analyze vulnerability and compliance with powerful dashboard reports.
STEP THREE
Security Policy Tracking & Compliance
Quickly upload your organization's security policies to our Security Policy Tracking & Compliance Service, then track reading and acceptance of security policies by employees, then view compliance reports online or download for your records. Automatically notify employees by email as soon as a new security policy is available to ensure policies don't go unnoticed.

STEP FOUR
Engage with Security Awareness Materials
Incorporate our high quality, graphical security awareness materials into your employee education program to reinforce cybersecurity messages and enhance retention. Grab employee attention, focus your cybersecurity message, and spread the word with these fun outreach materials.

How Can You Get Your Employees to Be Cyber Secure?
Take a quick tour of Security Mentor’s unrivaled security awareness training lessons and learn about our pioneering Brief, Frequent, Focused™ training model. Discover how you can help your employees to become cyber secure. Now imagine that employees want to take training, even thank you for it.

Testimonials & Clients
You could take our word that our customers and their employees love Security Mentor Training, or that you’ll see a reduction in risky behaviors by employees, but we think you’d rather hear what our customers themselves have to say.


Security Awareness Training that Makes a Difference
Isn’t all security awareness training alike? If I do phishing simulation, isn’t that enough? Reasonable questions, for sure, but the answer to both is NO. The success of your cyber security awareness program will determine if your employees understand information security and their ability to prevent security incidents. If training is boring, hard to understand, or not interactive, you’ve lost the battle. Learn why training is most successful when frequently given in small bites of sticky, targeted information that are reinforced over time.

Events & Presentations
News

Security Awareness Blog
The human factor in cybersecurity refers to the impact that an organization's employees, contractors, and third parties have on the cybersecurity of the organization, its information systems, and data. Although an organization's people are its greatest asset, they also can be one of the most significant vulnerabilities. Some common employee cyber errors include clicking on phishing links or opening malicious email attachments, sharing passwords, losing mobile devices, and putting sensitive information in the cloud. The best protection against human error is an effective cyber awareness program.
The human factor, or people, are the greatest cause of data breaches. The human element was involved in 85% of all breaches, according to the 2021 Data Breach Investigations Report (DBIR) from Verizon.
Before people can protect against cyber threats, or prevent their own cyber security mistakes, they must understand what the dangers are, why they matter, and what they can do to protect against cyberattacks and cyber security incidents. Cyber awareness training is the best way to teach employees about information security best practices, how cyber attacks happen, the consequences of human error, and to provide employees with the critical cyber security skills necessary to protect your organization and be cyber secure, both at work and at home.
- Get buy-in from executive management and their active participation in your cyber awareness program; it is key to the program's success
- Appoint a skilled, energetic, and effective training program manager
- Layout objectives and goals for your program
- Provide regular security awareness training that is both effective and focuses on the learner
- Create a culture of security so that employees can freely ask questions, as well as report incidents and mistakes
- Utilize multiple forms of awareness outreach in addition to training
- Ask employees for training feedback and incorporate their suggestions
There are five types of cyber security education given to employees:
- Security Awareness Training. Teaches general cyber security principles to all employees. You'll see this type of employee security training called by many other names, including cyber awareness training, cyber security awareness training, employee cybersecurity training and information security awareness training.
- Phishing Training. Focuses solely on teaching employees about phishing and how to avoid phishing attacks.
- Role-based Security Awareness Training. Targeted training that focuses on a specific job or role that an employee has; for example, system administration, management, or customer service.
- Information Security Training, also known as IT Security Training or Infosec Training. Designed to teach security staff, engineers and developers about technical aspects of cybersecurity, covering topics like secure coding practices, cyber attacks against infrastructure, and common vulnerabilities in technology.
- Information Assurance (IA) Training. IA Training is cyber security training provided to government and military staff and contractors. The primary focus of IA Training is the protection of information, software and hardware.
- Robust, relevant material covering key cyber security topics
- Use of games and other forms of interactive training
- High quality, engaging content
- Teaching of cyber skills, not just awareness
- High employee satisfaction
- High employee participation
- Phishing and email security
- Social media / social networking
- Mobile security
- Information protection
- Incident reporting
- Password security and password management
- Social engineering
- Insider threat
- Cloud security
- Office security and clean desk policies
An extra 11th topic is remote work security, which is an essential training if employees work remotely or are in hybrid office environments.
Training should be provided frequently so that it reinforces learning, and cybersecurity training is no exception. Employees should receive cyber awareness training on a regular basis. Brief training delivered monthly is an ideal balance between keeping cybersecurity top-of-mind, and having a minimal impact on employees' work productivity.
We've compiled a short list of some of the best web resources for eLearning and employee training. These websites provide information and resources on learning strategies and skills, eLearning theory, industry trends, workforce training, as well as new ideas for eLearning content and programs.
Learning Guild (formerly the eLearning Guild), eLearning Industry and eLearning Learning are all respected eLearning websites offering a wide array of resources, including thought leadership, white papers, eBooks, blogs, webinars, and podcasts. ATD (Association for Talent Development) is a professional organization for furthering skills in training and development. Training magazine and Chief Learning Officer are multimedia platforms providing resources aimed at training professionals and on the benefits of a properly trained workforce. Finally, the Harvard Business Review provides a wealth of information on business and management topics, including on eLearning, psychology, and marketing.
Cyber security terms, also referred to as cybersecurity terms, are words or phrases that specifically relate to the field cyber security, also referred to as cybersecurity.
There are two complimentary but different types of phishing training (also known as phishing awareness training.) The first and most common type of phishing training, called phishing testing, uses a phishing simulator to teach employees not to click on phishing links or open malicious attachments by running simulated phishing campaigns. Brief follow-up training is given to employees who fall for the attack. The second type of phishing training is a phishing awareness course, which provides much deeper training on what phishing is, the phishing tactics that phishers employ to manipulate their targets, and techniques on how to identify and avoid phishing scams. After completing a phishing awareness course, employees are better prepared to handle both current and evolving future phishing scams.
Phishing has become the preferred type of cyber attack for hackers to compromise public and private sector organizations, as well as individuals. Even with the sophisticated phishing protection software and systems that organizations deploy, phishing attacks still get through. This trend has only accelerated as more employees work remotely or in hybrid office environments where organizations have even less control over employee behavior. Therefore, it is essential to teach employees to defend themselves and their organizations against phishing, by learning how to identify, and not fall victim to, phishing attacks. This is exactly what a phishing test is designed to do.
A phishing simulator is an anti-phishing software or service that is used by organizations to measure the vulnerability of their staff to phishing scams by running simulated phishing campaigns. A phishing simulation mimics a real phishing attack by sending phishing tests to employees. The purpose of phishing simulations is to teach employees how to spot a phishing message and not fall victim to a real phishing attack. Most vendors offering phishing simulation services offer the following capabilities:
- A pre-built catalog of phishing templates or the ability to create your own phishing templates
- Ability to send phishing emails to the entire organization, or to target a specific group or individual
- Track employees' interactions with phishing tests, including phishing email opens, clicks and replies, phishing attachment opens, and web form fills
- Provide vulnerable employees, those that fall for phishing tests, with immediate, real-time training related to the specific attack
- A dashboard with phishing reports that graphically represent current and historical phishing campaign statistics
Cybersecurity frameworks, standards and controls help organizations manage risk; some well-known and trusted sources include: ISO 27001, System and Organization Controls (SOC), NIST Cybersecurity Framework, and CIS controls, and COBIT. The OWASP Top Ten provides guidance to organizations and developers on web application security.
An information security policy, or cybersecurity policy, is a policy that sets out the requirements for protecting information in an organization, including the types of information and systems that need to be protected and the ways in which they are protected. Information security policies may apply to people, processes, or systems; policies also may be organization-wide, or apply only to a specific subset. Various governmental regulations and industry standards require organizations to have information security policies, both in place and in practice, as part of compliance.
Security Mentor aggregates current cybersecurity statistics and trends on the human factor, data breaches, cybercrime, phishing, remote work, ransomware, passwords, insider threats, the COVID-19 pandemic, and much more. We also aggregate statistics and trends by industry vertical including, Financial Services, Healthcare, and Energy & Utilities. To see our report, go to Security Awareness Training Statistics & Trends: 2020-2021 Edition.
Security awareness materials are designed to raise the awareness of and remind employees about common cyber threats and how to protect against them. Cyber security awareness materials often address topics like phishing, password security, office security, lost or stolen mobile devices, and the exposure of sensitive information. Awareness materials also provide a different media for training that may be effective at reaching employees who are visual learners. Finally, alternate forms of training are required for some regulatory compliance, for example PCI DSS, which requires multiple forms of security awareness and training.
Common types of cyber awareness materials include posters, newsletters, cartoons, wallpapers for operating systems (also known as desktop wallpaper or desktop backgrounds), screen savers, even swag like clothing and mugs. Awareness materials can be recurring such as newsletters and posters, or a giveaway for a special event such as part of Cyber Security Awareness Month.